Serverless Architecture: Guide for Data Protection


With the rising popularity of serverless computing, more and more organizations are shifting their workloads to the cloud. The serverless architecture offers several benefits, including cost savings, scalability, and increased productivity. However, with these advantages come new security challenges that organizations must address to protect their data. In a serverless environment, the responsibility for security shifts from the infrastructure to the application, which can leave vulnerabilities if not properly secured. Businesses must implement the best serverless security practices to protect their sensitive data. It includes ensuring proper authentication and authorization mechanisms, encrypting data in transit and at rest, and monitoring potential security breaches.
This article will discuss what serverless computing is and the tips and tricks for securing your serverless architecture and protecting your data in the cloud.
What is Serverless Architecture?
Serverless architecture is a computing model that allows organizations to build and run applications without managing the underlying infrastructure. With serverless architecture, the cloud provider takes responsibility for the infrastructure, such as servers, operating systems, and storage, freeing up the organization to focus on developing and deploying their applications.
In a serverless environment, applications are broken down into smaller, independent functions that can be executed on demand. These functions are triggered by specific events, such as user requests or changes to data, and are automatically scaled up or down based on need. This allows organizations to only pay for their resources, making it a more cost-effective solution than traditional infrastructure models.
Serverless architecture offers several benefits, including improved scalability, lower operational costs, increased productivity, and reduced time-to-market. It is also easier to manage and maintain since the cloud provider handles the infrastructure. In short, Serverless architecture is a powerful and innovative way to build and deploy applications in the cloud. It enables organizations to focus on delivering high-quality applications while leveraging the benefits of the cloud without the burden of managing infrastructure.
Serverless Vs. Traditional Architecture
Serverless computing has emerged as a popular choice for building and deploying modern applications due to its scalability, cost-effectiveness, and reduced management overhead. In contrast, traditional architecture requires maintaining infrastructure, provisioning servers, and managing software updates, making it more resource-intensive and time-consuming.
Serverless architecture allows developers to focus on writing code without worrying about the underlying infrastructure. This is possible using cloud providers’ serverless computing services such as AWS Lambda, Azure Functions, and Google Cloud Functions. These services provide automatic scaling, allowing applications to handle large traffic spikes without manual intervention. Moreover, serverless architectures can reduce costs by only charging for the number of resources used, making them an attractive option for startups and small businesses.

However, serverless computing also presents unique security challenges. As data is processed in the cloud, there is an increased risk of unauthorized access or data breaches. This makes data protection a crucial concern for organizations using serverless architectures. Encryption is one of the most effective ways to secure data in transit and, at rest, protect it from unauthorized access. Access controls, such as Identity and Access Management (IAM), can also ensure only authorized users have access to sensitive data.
API security is another critical aspect of serverless architecture. As APIs are used to connect different services in serverless computing, they need to be secured to prevent attackers from exploiting vulnerabilities in the system. API security measures, such as rate limiting, authentication, and authorization, can prevent unauthorized access and protect against malicious attacks.
In comparison, traditional architecture involves maintaining servers and databases, requiring additional security measures to protect against threats such as distributed denial of service (DDoS) attacks and malware. Container security is also essential in traditional architectures, as containers can be compromised if not appropriately secured.
Best Practices For Serverless Security

Serverless architecture offers numerous benefits, such as reduced management overhead and cost-effectiveness. However, as data processing is done in the cloud, it is crucial to implement robust security measures to protect against potential threats. Here are some best practices for securing serverless architecture:
Least Privilege Principle
The least privilege principle is a crucial security best practice in a serverless architecture. It involves granting only the necessary permissions to your serverless functions to access specific resources rather than giving them broad access. Doing so can reduce the risk of unauthorized access and minimize the damage in the event of a breach.
To implement the least privilege principle, you can use identity and access management (IAM) policies to define the specific permissions that each function needs. IAM policies can grant permissions to specific resources, such as AWS S3 buckets or DynamoDB tables. They can also limit a function’s actions, such as read-only access or write access. In addition to using IAM policies, it is essential to regularly review and update permissions to ensure that they are still necessary and appropriate. This can help prevent permissions from accumulating over time, which can increase the risk of a security breach. By applying the least privilege principle, you can enhance the security of your serverless architecture and ensure that your applications remain protected against potential threats.
Function Hardening
Function hardening is a crucial security practice in serverless architecture that involves taking steps to reduce the attack surface of your functions. By doing so, you can minimize the risk of malicious actors exploiting vulnerabilities in your code and potentially gaining unauthorized access to your systems. One way to harden your functions is to implement runtime protection measures, such as code obfuscation or encryption. These techniques can make it more difficult for attackers to reverse engineer your code and discover potential vulnerabilities.

Another approach is to implement input validation and output sanitization measures to prevent injection attacks. These measures include validating user input to ensure it meets specific criteria and sanitizing output to remove potentially dangerous code or characters. In addition to these measures, it is essential to follow secure coding practices when developing your functions, such as avoiding hard-coded credentials and using parameterized SQL queries to prevent SQL injection attacks. By implementing function hardening measures, you can enhance the security of your serverless architecture and help protect against potential threats.
Secure Secrets Management
Secure secrets management is a crucial security practice in serverless architecture that involves securely storing and managing sensitive data, such as API keys, passwords, and other credentials. Failure to adequately secure these secrets can leave your system vulnerable to attack and potentially compromise your infrastructure.

You can use AWS Secrets Manager or HashiCorp Vault to securely store and manage your secrets. These tools provide encryption, access control, and auditing features, ensuring that your secrets are only accessible to authorized users and applications. In addition to using these tools, it is essential to follow secure practices when handling secrets, such as rotating them regularly, restricting access to only those who need it, and monitoring access to detect any unauthorized activity. By implementing secure secrets management practices, you can significantly reduce the risk of a security breach and ensure that your serverless architecture remains protected against potential threats.
Secure Deployment Pipelines
Secure deployment pipelines are a crucial security practice in serverless architecture that involves implementing security measures throughout the deployment. This helps ensure your applications are securely deployed, and your infrastructure remains protected against potential threats.
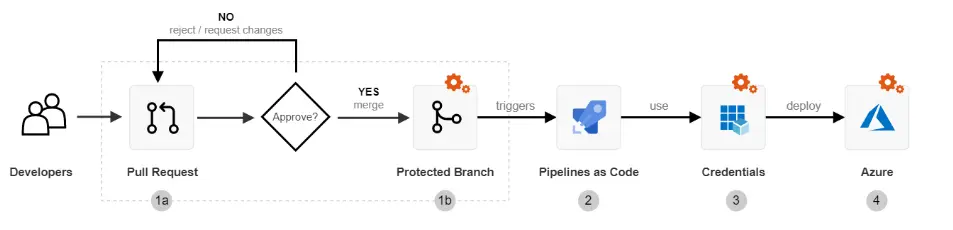
It is recommended to use AWS CodePipeline or Jenkins to automate the deployment process and include security checks at each stage. For example, you can use automated vulnerability scanning and testing in your deployment pipeline to detect potential vulnerabilities or weaknesses in your code. You can also use infrastructure-as-code tools, such as AWS CloudFormation or Terraform, to automate the deployment of your serverless applications and infrastructure. This can help ensure that your infrastructure is consistently and securely deployed, reducing the risk of human error and misconfiguration. In addition to these measures, it is essential to regularly review and update your deployment pipeline to ensure that it remains secure and up-to-date with the latest security best practices. By implementing secure deployment pipelines, you can significantly enhance the security of your serverless architecture and ensure that your applications and infrastructure remain protected against potential threats.
Runtime Application Self-Protection (RASP)
Runtime application self-protection (RASP) is a security technology that helps protect serverless applications by embedding security controls within the application. Unlike traditional security measures at the perimeter, RASP is designed to detect and prevent attacks in real time as they occur. RASP works by monitoring the behavior of an application at runtime and detecting any abnormal activity or potential security threats. On a threat detection, RASP can immediately prevent the attack from succeeding, such as blocking the request or terminating the session.
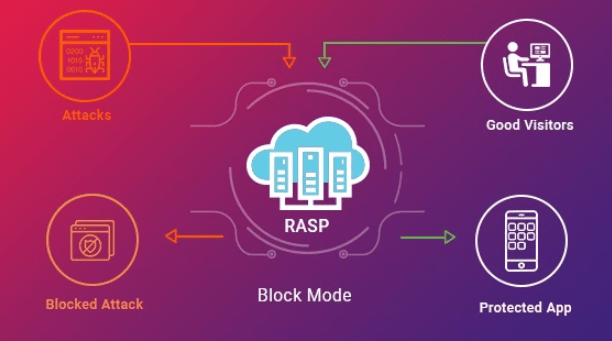
RASP can provide additional security features like data encryption, access control, and audit logging. These features help protect sensitive data, only authorized users can access the application, and any potential security incidents is traceable. By embedding security controls within the application, RASP can provide a more comprehensive and proactive approach to security, helping to protect against a wide range of potential threats. However, it should be noted that RASP is not a replacement for other security measures and should be used in conjunction with other security practices to ensure a robust and secure serverless architecture.
Automated Scanning and Remediation
Automated scanning and remediation is a serverless security practice involving computerized tools to scan and detect potential vulnerabilities or weaknesses in your serverless infrastructure or applications. Once vulnerabilities are detected, these tools can automatically remediate the issues, helping to ensure that your serverless architecture remains secure and protected against potential attacks. Various tools are available for automated scanning and remediation, including vulnerability scanners and security testing tools. These tools can be integrated into your deployment pipeline and scan your infrastructure and applications at various development and deployment stages, including testing, staging, and production.

Automated scanning and remediation can significantly improve the security of your serverless architecture by detecting and fixing vulnerabilities before attackers can exploit them. It can also help reduce the workload on your security team, as it can automate many routine security checks However, It is crucial to ensure that these tools are working correctly and get updates regularly to detect and remediating the latest security threats. Additionally, manual security checks and reviews should still be routinely performed to supplement automated tools and ensure a comprehensive approach to serverless security.
Compliance Monitoring and Reporting
Compliance monitoring and reporting is a serverless security practice that involves regular monitoring and reporting on your serverless infrastructure and applications. It is done to ensure they comply with relevant security regulations and standards. Compliance requirements can vary depending on your organization’s industry and geographic location. Still, typical examples include HIPAA for healthcare data, PCI DSS for payment card data, and GDPR for personal data protection.

By implementing compliance monitoring and reporting, you can ensure that your serverless architecture meets these requirements and avoid potential legal and financial consequences for non-compliance. Compliance monitoring and reporting involve reviewing logs and other relevant data to ensure security controls are in place and functioning as intended. The automated tools can also help in identifying any potential compliance issues. Regular reporting to internal stakeholders and regulatory bodies can also demonstrate that your organization is taking security seriously and proactively working to maintain compliance. Compliance monitoring and reporting is an essential aspects of serverless security, helping to ensure that your serverless architecture meets legal and regulatory requirements and protecting your organization from potential security risks.
Distributed Denial of Service (DDoS)
Distributed Denial of Service (DDoS) attacks significantly threaten serverless architectures. In a DDoS attack, many compromised computers, also known as a botnet, flood a server or network with requests, overwhelming it and causing it to crash. The impact of a DDoS attack on a serverless architecture can be severe, as it can cause downtime, data loss, and reputational damage. Therefore, implementing measures to prevent and mitigate DDoS attacks is crucial.
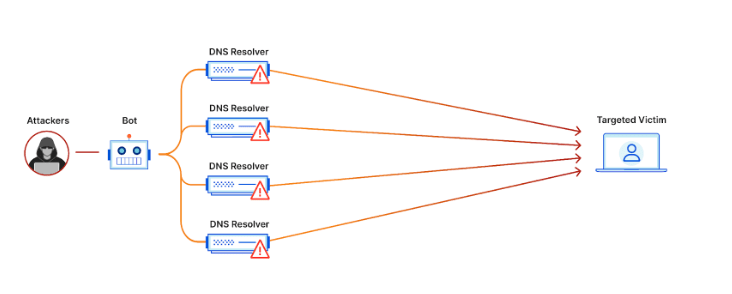
One practical approach is to use a content delivery network (CDN) to distribute traffic across multiple servers, making it harder for attackers to overload a single server. Another approach is to use rate limiting and access control mechanisms to limit the number of requests from a single IP address or user. It is also essential to have a plan to detect and respond to DDoS attacks in real-time, including monitoring network traffic and setting up alerts to notify administrators of unusual activity. DDoS attacks are a significant threat to serverless architectures. Organizations should take proactive steps to prevent and mitigate them to ensure the availability and security of their applications and data.
Protection Security Information and Event Management (SIEM)
Protection Security Information and Event Management (SIEM) is a critical component of serverless security. It is a system that collects and analyzes security-related data from various sources in real-time to detect and respond to security incidents. A SIEM system provides visibility into the security posture of a serverless architecture by collecting and correlating security events from various sources, including server logs, application logs, network traffic, and cloud provider APIs. By analyzing this data, it can identify potential security threats, such as unauthorized access attempts, malware infections, or data exfiltration.
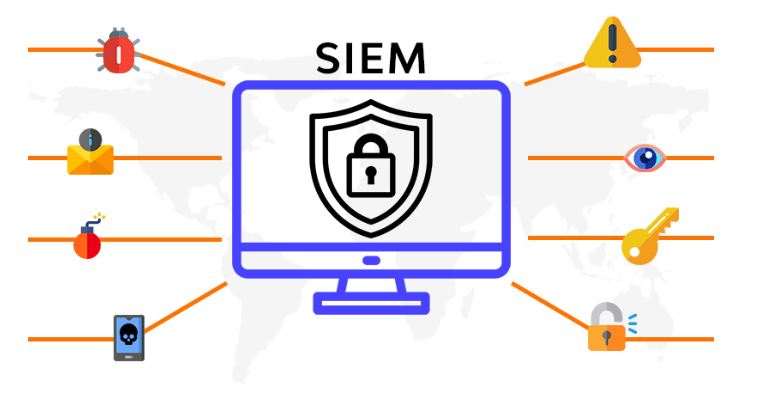
SIEM systems can also provide automated responses to security incidents, such as blocking an IP address or user account, sending alerts to security teams, or triggering other security controls. To effectively protect a serverless architecture, it is essential to configure the SIEM system with the appropriate log sources, filters, and correlation rules. It is also essential to continuously monitor and tune the SIEM system to ensure that it provides accurate and relevant alerts. A SIEM system is a crucial component of serverless security, providing real-time visibility and response capabilities to help detect and mitigate security threats in a serverless environment.
Threat Modeling and Risk Assessment
Threat modeling and risk assessment are critical processes that help organizations identify and mitigate potential security risks in their serverless architecture. By conducting a thorough threat modeling exercise, developers can identify potential threats to their applications and infrastructure, evaluate their impact, and prioritize the appropriate security controls to mitigate them.
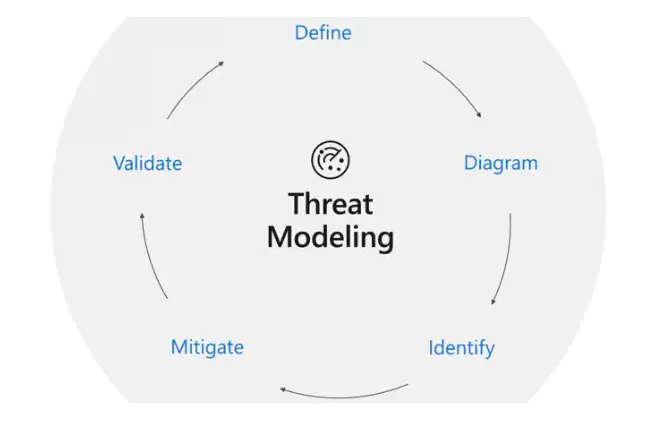
Risk assessment is analyzing potential risks and assessing their likelihood and impact. By conducting a comprehensive risk assessment, organizations can identify their most critical assets and the most significant risks to those assets. This information is beneficial in prioritizing security efforts and allocating resources appropriately. Threat modeling and risk assessment provide a holistic approach to serverless security. They help organizations identify potential vulnerabilities, prioritize remediation efforts, and allocate resources effectively. By taking these steps, organizations can ensure their serverless architecture is secure and resilient to the ever-evolving threat landscape.
Final Words
Securing your serverless architecture is crucial to protect your data and to ensure the safety of your applications. You can minimize the risk of potential threats and attacks by following best practices such as implementing the least privilege principle, function hardening, secure secrets management, and compliance monitoring. Additionally, utilizing runtime application self-protection, automated scanning and remediation, DDoS protection, and security information and event management can provide added layers of security. Threat modeling and risk assessment are also essential in identifying and addressing potential vulnerabilities. By adopting these practices, you can enhance the security of your serverless architecture and mitigate potential risks to your data and applications.
Tagged
Share This Article
With the rising popularity of serverless computing, more and more organizations are shifting their workloads to the cloud. The serverless architecture offers several benefits, including cost savings, scalability, and increased productivity. However, with these advantages come new security challenges that organizations must address to protect their data. In a serverless environment, the responsibility for security shifts from the infrastructure to the application, which can leave vulnerabilities if not properly secured. Businesses must implement the best serverless security practices to protect their sensitive data. It includes ensuring proper authentication and authorization mechanisms, encrypting data in transit and at rest, and monitoring potential security breaches.
This article will discuss what serverless computing is and the tips and tricks for securing your serverless architecture and protecting your data in the cloud.
What is Serverless Architecture?
Serverless architecture is a computing model that allows organizations to build and run applications without managing the underlying infrastructure. With serverless architecture, the cloud provider takes responsibility for the infrastructure, such as servers, operating systems, and storage, freeing up the organization to focus on developing and deploying their applications.
In a serverless environment, applications are broken down into smaller, independent functions that can be executed on demand. These functions are triggered by specific events, such as user requests or changes to data, and are automatically scaled up or down based on need. This allows organizations to only pay for their resources, making it a more cost-effective solution than traditional infrastructure models.
Serverless architecture offers several benefits, including improved scalability, lower operational costs, increased productivity, and reduced time-to-market. It is also easier to manage and maintain since the cloud provider handles the infrastructure. In short, Serverless architecture is a powerful and innovative way to build and deploy applications in the cloud. It enables organizations to focus on delivering high-quality applications while leveraging the benefits of the cloud without the burden of managing infrastructure.
Serverless Vs. Traditional Architecture
Serverless computing has emerged as a popular choice for building and deploying modern applications due to its scalability, cost-effectiveness, and reduced management overhead. In contrast, traditional architecture requires maintaining infrastructure, provisioning servers, and managing software updates, making it more resource-intensive and time-consuming.
Serverless architecture allows developers to focus on writing code without worrying about the underlying infrastructure. This is possible using cloud providers’ serverless computing services such as AWS Lambda, Azure Functions, and Google Cloud Functions. These services provide automatic scaling, allowing applications to handle large traffic spikes without manual intervention. Moreover, serverless architectures can reduce costs by only charging for the number of resources used, making them an attractive option for startups and small businesses.

However, serverless computing also presents unique security challenges. As data is processed in the cloud, there is an increased risk of unauthorized access or data breaches. This makes data protection a crucial concern for organizations using serverless architectures. Encryption is one of the most effective ways to secure data in transit and, at rest, protect it from unauthorized access. Access controls, such as Identity and Access Management (IAM), can also ensure only authorized users have access to sensitive data.
API security is another critical aspect of serverless architecture. As APIs are used to connect different services in serverless computing, they need to be secured to prevent attackers from exploiting vulnerabilities in the system. API security measures, such as rate limiting, authentication, and authorization, can prevent unauthorized access and protect against malicious attacks.
In comparison, traditional architecture involves maintaining servers and databases, requiring additional security measures to protect against threats such as distributed denial of service (DDoS) attacks and malware. Container security is also essential in traditional architectures, as containers can be compromised if not appropriately secured.
Best Practices For Serverless Security

Serverless architecture offers numerous benefits, such as reduced management overhead and cost-effectiveness. However, as data processing is done in the cloud, it is crucial to implement robust security measures to protect against potential threats. Here are some best practices for securing serverless architecture:
Least Privilege Principle
The least privilege principle is a crucial security best practice in a serverless architecture. It involves granting only the necessary permissions to your serverless functions to access specific resources rather than giving them broad access. Doing so can reduce the risk of unauthorized access and minimize the damage in the event of a breach.
To implement the least privilege principle, you can use identity and access management (IAM) policies to define the specific permissions that each function needs. IAM policies can grant permissions to specific resources, such as AWS S3 buckets or DynamoDB tables. They can also limit a function’s actions, such as read-only access or write access. In addition to using IAM policies, it is essential to regularly review and update permissions to ensure that they are still necessary and appropriate. This can help prevent permissions from accumulating over time, which can increase the risk of a security breach. By applying the least privilege principle, you can enhance the security of your serverless architecture and ensure that your applications remain protected against potential threats.
Function Hardening
Function hardening is a crucial security practice in serverless architecture that involves taking steps to reduce the attack surface of your functions. By doing so, you can minimize the risk of malicious actors exploiting vulnerabilities in your code and potentially gaining unauthorized access to your systems. One way to harden your functions is to implement runtime protection measures, such as code obfuscation or encryption. These techniques can make it more difficult for attackers to reverse engineer your code and discover potential vulnerabilities.

Another approach is to implement input validation and output sanitization measures to prevent injection attacks. These measures include validating user input to ensure it meets specific criteria and sanitizing output to remove potentially dangerous code or characters. In addition to these measures, it is essential to follow secure coding practices when developing your functions, such as avoiding hard-coded credentials and using parameterized SQL queries to prevent SQL injection attacks. By implementing function hardening measures, you can enhance the security of your serverless architecture and help protect against potential threats.
Secure Secrets Management
Secure secrets management is a crucial security practice in serverless architecture that involves securely storing and managing sensitive data, such as API keys, passwords, and other credentials. Failure to adequately secure these secrets can leave your system vulnerable to attack and potentially compromise your infrastructure.

You can use AWS Secrets Manager or HashiCorp Vault to securely store and manage your secrets. These tools provide encryption, access control, and auditing features, ensuring that your secrets are only accessible to authorized users and applications. In addition to using these tools, it is essential to follow secure practices when handling secrets, such as rotating them regularly, restricting access to only those who need it, and monitoring access to detect any unauthorized activity. By implementing secure secrets management practices, you can significantly reduce the risk of a security breach and ensure that your serverless architecture remains protected against potential threats.
Secure Deployment Pipelines
Secure deployment pipelines are a crucial security practice in serverless architecture that involves implementing security measures throughout the deployment. This helps ensure your applications are securely deployed, and your infrastructure remains protected against potential threats.

It is recommended to use AWS CodePipeline or Jenkins to automate the deployment process and include security checks at each stage. For example, you can use automated vulnerability scanning and testing in your deployment pipeline to detect potential vulnerabilities or weaknesses in your code. You can also use infrastructure-as-code tools, such as AWS CloudFormation or Terraform, to automate the deployment of your serverless applications and infrastructure. This can help ensure that your infrastructure is consistently and securely deployed, reducing the risk of human error and misconfiguration. In addition to these measures, it is essential to regularly review and update your deployment pipeline to ensure that it remains secure and up-to-date with the latest security best practices. By implementing secure deployment pipelines, you can significantly enhance the security of your serverless architecture and ensure that your applications and infrastructure remain protected against potential threats.
Runtime Application Self-Protection (RASP)
Runtime application self-protection (RASP) is a security technology that helps protect serverless applications by embedding security controls within the application. Unlike traditional security measures at the perimeter, RASP is designed to detect and prevent attacks in real time as they occur. RASP works by monitoring the behavior of an application at runtime and detecting any abnormal activity or potential security threats. On a threat detection, RASP can immediately prevent the attack from succeeding, such as blocking the request or terminating the session.

RASP can provide additional security features like data encryption, access control, and audit logging. These features help protect sensitive data, only authorized users can access the application, and any potential security incidents is traceable. By embedding security controls within the application, RASP can provide a more comprehensive and proactive approach to security, helping to protect against a wide range of potential threats. However, it should be noted that RASP is not a replacement for other security measures and should be used in conjunction with other security practices to ensure a robust and secure serverless architecture.
Automated Scanning and Remediation
Automated scanning and remediation is a serverless security practice involving computerized tools to scan and detect potential vulnerabilities or weaknesses in your serverless infrastructure or applications. Once vulnerabilities are detected, these tools can automatically remediate the issues, helping to ensure that your serverless architecture remains secure and protected against potential attacks. Various tools are available for automated scanning and remediation, including vulnerability scanners and security testing tools. These tools can be integrated into your deployment pipeline and scan your infrastructure and applications at various development and deployment stages, including testing, staging, and production.

Automated scanning and remediation can significantly improve the security of your serverless architecture by detecting and fixing vulnerabilities before attackers can exploit them. It can also help reduce the workload on your security team, as it can automate many routine security checks However, It is crucial to ensure that these tools are working correctly and get updates regularly to detect and remediating the latest security threats. Additionally, manual security checks and reviews should still be routinely performed to supplement automated tools and ensure a comprehensive approach to serverless security.
Compliance Monitoring and Reporting
Compliance monitoring and reporting is a serverless security practice that involves regular monitoring and reporting on your serverless infrastructure and applications. It is done to ensure they comply with relevant security regulations and standards. Compliance requirements can vary depending on your organization’s industry and geographic location. Still, typical examples include HIPAA for healthcare data, PCI DSS for payment card data, and GDPR for personal data protection.

By implementing compliance monitoring and reporting, you can ensure that your serverless architecture meets these requirements and avoid potential legal and financial consequences for non-compliance. Compliance monitoring and reporting involve reviewing logs and other relevant data to ensure security controls are in place and functioning as intended. The automated tools can also help in identifying any potential compliance issues. Regular reporting to internal stakeholders and regulatory bodies can also demonstrate that your organization is taking security seriously and proactively working to maintain compliance. Compliance monitoring and reporting is an essential aspects of serverless security, helping to ensure that your serverless architecture meets legal and regulatory requirements and protecting your organization from potential security risks.
Distributed Denial of Service (DDoS)
Distributed Denial of Service (DDoS) attacks significantly threaten serverless architectures. In a DDoS attack, many compromised computers, also known as a botnet, flood a server or network with requests, overwhelming it and causing it to crash. The impact of a DDoS attack on a serverless architecture can be severe, as it can cause downtime, data loss, and reputational damage. Therefore, implementing measures to prevent and mitigate DDoS attacks is crucial.

One practical approach is to use a content delivery network (CDN) to distribute traffic across multiple servers, making it harder for attackers to overload a single server. Another approach is to use rate limiting and access control mechanisms to limit the number of requests from a single IP address or user. It is also essential to have a plan to detect and respond to DDoS attacks in real-time, including monitoring network traffic and setting up alerts to notify administrators of unusual activity. DDoS attacks are a significant threat to serverless architectures. Organizations should take proactive steps to prevent and mitigate them to ensure the availability and security of their applications and data.
Protection Security Information and Event Management (SIEM)
Protection Security Information and Event Management (SIEM) is a critical component of serverless security. It is a system that collects and analyzes security-related data from various sources in real-time to detect and respond to security incidents. A SIEM system provides visibility into the security posture of a serverless architecture by collecting and correlating security events from various sources, including server logs, application logs, network traffic, and cloud provider APIs. By analyzing this data, it can identify potential security threats, such as unauthorized access attempts, malware infections, or data exfiltration.

SIEM systems can also provide automated responses to security incidents, such as blocking an IP address or user account, sending alerts to security teams, or triggering other security controls. To effectively protect a serverless architecture, it is essential to configure the SIEM system with the appropriate log sources, filters, and correlation rules. It is also essential to continuously monitor and tune the SIEM system to ensure that it provides accurate and relevant alerts. A SIEM system is a crucial component of serverless security, providing real-time visibility and response capabilities to help detect and mitigate security threats in a serverless environment.
Threat Modeling and Risk Assessment
Threat modeling and risk assessment are critical processes that help organizations identify and mitigate potential security risks in their serverless architecture. By conducting a thorough threat modeling exercise, developers can identify potential threats to their applications and infrastructure, evaluate their impact, and prioritize the appropriate security controls to mitigate them.

Risk assessment is analyzing potential risks and assessing their likelihood and impact. By conducting a comprehensive risk assessment, organizations can identify their most critical assets and the most significant risks to those assets. This information is beneficial in prioritizing security efforts and allocating resources appropriately. Threat modeling and risk assessment provide a holistic approach to serverless security. They help organizations identify potential vulnerabilities, prioritize remediation efforts, and allocate resources effectively. By taking these steps, organizations can ensure their serverless architecture is secure and resilient to the ever-evolving threat landscape.
Final Words
Securing your serverless architecture is crucial to protect your data and to ensure the safety of your applications. You can minimize the risk of potential threats and attacks by following best practices such as implementing the least privilege principle, function hardening, secure secrets management, and compliance monitoring. Additionally, utilizing runtime application self-protection, automated scanning and remediation, DDoS protection, and security information and event management can provide added layers of security. Threat modeling and risk assessment are also essential in identifying and addressing potential vulnerabilities. By adopting these practices, you can enhance the security of your serverless architecture and mitigate potential risks to your data and applications.




![How To Fake GPS Location on iPhone Without Jailbreaking [2023]](/_next/image?url=https%3A%2F%2Fwriteflow-media.s3.amazonaws.com%2Fsites%2F16%2Fmedia%2F2025%2F10%2Fgps-location-feature-wlaR2F.webp&w=3840&q=75)