Code and data protection are essential components of modern technology. With cyber threats becoming increasingly sophisticated and numerous, it’s important to take proactive measures to protect your code and data.
This article will explore 10 cybersecurity and ethical hacking tips that can help you protect your code and data from unauthorized access and malicious attacks. We will discuss the importance of maintaining strong passwords, implementing two-factor authentication, keeping your software up to date, and using encryption to protect sensitive data. We will also cover the importance of conducting regular vulnerability assessments, training employees on cybersecurity best practices, and implementing network segmentation. By following these tips, you can help prevent cyber attacks and keep your code and data secure.
So let’s dive in and learn how to safeguard our digital assets in today’s ever-changing technological landscape!
10 Cybersecurity And Ethical Hacking Tips

Fortress Locks: Building Impenetrable Passwords and Passphrases
Passwords and passphrases are the first line of defense when protecting your code and data. Unfortunately, many users still rely on easily guessable passwords, such as “123456” or “password” leaving them vulnerable to cyber-attacks. To ensure your passwords and passphrases are truly impenetrable, it’s important to follow some key guidelines.

A strong password should contain at least 12 characters, including upper and lowercase letters, numbers, and symbols. Avoid using common words, phrases, or personal information, such as your name, birthdate, or address. Instead, consider using a passphrase, which is a series of unrelated words strung together to form a sentence, such as “pencilapplecartfire.“
Use a password manager to generate and store your passwords securely. This will help you avoid reusing passwords across different accounts, which can make you more vulnerable to cyber-attacks. Many password managers also come with a feature that helps you identify and replace weak passwords.
Consider implementing multi-factor authentication (MFA) to add an extra layer of security to your accounts (discussed below in detail). MFA requires users to provide additional authentication factors, such as a fingerprint or a security token, in addition to a password, making it much harder for cybercriminals to gain unauthorized access to your code and data.
Implementing strong passwords and passphrases is essential for code and data protection. Recently, major companies such as LinkedIn, Yahoo, and Equifax have experienced data breaches that have compromised millions of user accounts due to weak passwords. However, following these or any effective guidelines developed within your organization can significantly reduce the risk of a successful cyber attack on your code and data.
Double Protection: Two-Factor Authentication for Code and Data Security
Hackers can easily obtain passwords through various means, such as phishing scams, social engineering, or brute-force attacks. That’s why two-factor authentication (2FA) has become an essential code and data protection tool. 2FA provides an additional layer of security by requiring users to provide a second form of authentication, such as a fingerprint scan or a one-time code (OTP) sent to a mobile device, in addition to a password.
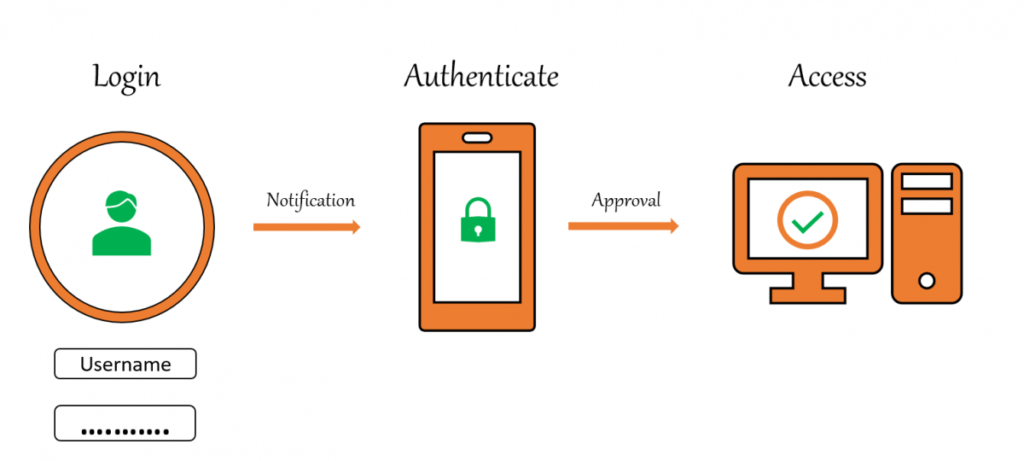
Real-world examples of the importance of 2FA include the 2017 Equifax data breach. In this incident, hackers gained access to the personal information of over 143 million people, largely due to the company’s lack of 2FA. In contrast, Google’s implementation of 2FA has significantly reduced the number of compromised accounts. The company reporting in 2019 that fewer than 0.1% of Google account users were impacted by phishing attacks.
To implement 2FA, check whether your online accounts offer this feature. Popular services such as Google, Apple, and Facebook all offer 2FA options. Once enabled, you’ll typically be prompted to provide a second form of authentication upon logging in, such as a one-time code sent to your mobile device or a fingerprint scan. For increased security, consider using a hardware token or security key, which provides additional protection against phishing attacks. These devices generate a unique code for each login attempt, which must be entered in addition to your password and other forms of authentication.
2FA is a simple but effective way to improve your code and data security significantly. Adding an extra layer of authentication can reduce the risk of successful cyber attacks and ensure that your sensitive information remains safe and secure.
Stay Ahead of the Game: The Importance of Keeping Software Up-to-Date
Keeping software up-to-date is crucial for code and data protection. As software vulnerabilities are constantly being discovered, updates and patches are released to address these issues and prevent hackers from exploiting them. Failure to install these updates can leave your system vulnerable to cyber-attacks and compromise your sensitive data.

We have seen the WannaCry ransomware attack in 2017, which affected hundreds of thousands of computers worldwide. This attack exploited a vulnerability in Microsoft’s Windows operating system that had already been patched by the company. However, many users failed to install the update, leaving their systems vulnerable to the attack. To ensure that your software is up-to-date, enable automatic updates wherever possible. This will ensure your software runs the latest version with the most recent security patches. Additionally, regularly check for updates and install them promptly to ensure maximum protection against potential cyber threats.
Keeping your software up-to-date is a simple but effective way to stay ahead of the game regarding code and data protection. By ensuring that your software is always running the latest version, you can minimize the risk of cyber-attacks and keep your sensitive information safe and secure.
Cipher Shield: The Power of Data Encryption for Code and Data Protection
The digital world is full of risks and dangers, making data encryption an indispensable tool to protect code and data from unauthorized access and cyber threats. Encryption involves using advanced algorithms to transform plain text into unreadable ciphertext, which can only be deciphered with a secret key. This process adds an extra layer of security to sensitive information, making it almost impossible for hackers to access or steal it.

The need for data encryption is highlighted by several high-profile data breaches that have occurred in recent years. Target, one of the largest retailers in the US, suffered a significant data breach in 2013 that resulted in the theft of millions of customer’s personal and financial data. The attack was successful because the data was not encrypted, underlining the importance of encryption in safeguarding sensitive data.
To implement data encryption, you must first identify the data that needs protection and determine the appropriate encryption standards to apply. Data can be encrypted at rest, in transit, or in use, depending on the situation. Many encryption tools and software are available to encrypt data, and it is essential to choose the most suitable encryption method based on the specific requirements. Data encryption is essential to protect code and data from unauthorized access and cyber threats. Strong encryption standards and practices can safeguard your sensitive information against potential cyber-attacks, ensuring your data remains secure and confidential.
Safe Haven: Regular Data Backups for Code and Data Protection
Another important step in ensuring code and data protection is regular data backups. Backups provide a safe haven for data in case of unexpected events, such as hardware failure, cyber-attacks, or natural disasters. By creating backups, you can quickly recover data in case of data loss, minimizing the impact on your business operations.

In 2017, a ransomware attack hit the global shipping company Maersk, resulting in significant data loss. However, because the company had backups in place, it could restore its operations within ten days, minimizing the financial impact of the attack. It is important to identify the critical data that needs to be backed up, the backup frequency, and the storage location. It is also crucial to test backups regularly to ensure their reliability in case of data loss.
Regular backups provide added security and peace of mind, allowing you to continue your operations with minimal disruption. Backing up your data can make a significant difference in the event of data loss, and it should be an integral part of any code and data protection strategy. You can use cloud-based storage solutions or external hard drives to implement data backups. It is recommended to have multiple copies of backups, with at least one copy stored offsite in case of physical damage to your primary storage location. Additionally, you should schedule regular backups at a frequency that aligns with your business needs and ensure that backups are tested regularly to ensure their reliability.
Network Armor: Securing Your Infrastructure with Secure Network Configuration
In today’s interconnected world, securing network configuration is essential for safeguarding code and data from unauthorized access, modification, or disruption. Network security involves securing the computer network infrastructure, including hardware, software, and policies, from various types of network security threats like malware, phishing attacks, and social engineering.

The importance of secure network configuration is evident by again going through the incident of Equifax. Organizations need to understand the different types of network security threats and take measures such as implementing a network security policy, configuring firewalls, and using intrusion detection and prevention systems. These measures can help secure network configurations and prevent data breaches, system downtime, and unauthorized access to sensitive data. Organizations can significantly impact their systems by implementing secure network configurations. They can ensure that their code and data are safe from cyber threats and that their business operations run smoothly without interruptions. It is essential for organizations to implement robust security measures to safeguard their network infrastructure from cyber threats.
Divide and Conquer: Implementing Network Segmentation for Code and Data Protection
Network segmentation is a highly effective technique for protecting code and data, especially in large organizations with complex network structures. This technique involves dividing a network into smaller, isolated segments, each with its own access permissions, policies, and security controls. Several real-world examples demonstrate the importance of network segmentation.

Businesses must first identify their network assets and the data they need to protect. Next, they should group similar assets and data into separate segments based on their security requirements and risk profile. Each segment should have its own monitoring systems, access controls, and firewalls to prevent unauthorized access and detect unusual activity. Network segmentation significantly enhances code and data protection by limiting the impact of cyber-attacks and preventing unauthorized access to sensitive data. It also improves network performance and simplifies network management by reducing the overall infrastructure’s complexity.
Cyber Sleuth: Conducting Regular Vulnerability Assessments to Protect Your Code and Data
Ensuring the protection of code and data requires a proactive approach to cybersecurity, which includes regular vulnerability assessments. Vulnerability assessments involve evaluating an organization’s network infrastructure, applications, and systems to identify potential vulnerabilities.

Recent events have shown that even the most popular and widely used applications can have vulnerabilities that cybercriminals can exploit. For example, in 2020, a vulnerability in the popular video conferencing app Zoom allowed attackers to gain unauthorized access to sensitive information.
In this practice, businesses must identify and prioritize their network assets based on their criticality. They can then use vulnerability scanning tools to detect and classify potential vulnerabilities based on their severity and potential impact. Regular vulnerability assessments can significantly enhance code and data protection by reducing the risk of cyber-attacks and data breaches, ensuring compliance with regulatory requirements, and improving the overall security posture.
Human Firewall: The Importance of Employee Cybersecurity Training
Cyber-attacks are becoming more frequent and sophisticated today, making employee cybersecurity training a critical component of code and data protection. Cybercriminals often target employees with phishing emails or other social engineering techniques to access an organization’s sensitive information.

Businesses should start with identifying the most common cyber threats and developing training materials to educate employees on how to recognize and respond to these threats. Training should be ongoing and regularly updated to address emerging cyber threats.
Effective employee cybersecurity training includes:
- Use real-world examples to demonstrate the impact of cyber attacks on the organization and its customers.
- Provide practical guidance on how to create strong passwords and protect personal information.
- Encourage employees to report any suspicious emails or activities to the IT department.
Effective employee cybersecurity training can significantly improve code and data protection by reducing the risk of human error and ensuring employees are aware of the best practices for protecting sensitive information.
Hack Yourself First: The Benefits of Ethical Hacking and Penetration Testing for Code and Data Protection
Cyber attacks are becoming more sophisticated and widespread, making it essential for organizations to stay ahead of the game in terms of code and data protection. Ethical hacking and penetration testing are two techniques that can help organizations identify system vulnerabilities and improve security measures.

Imagine a scenario where a hacker breaches an organization’s system and gains access to sensitive data, resulting in a data breach. This could lead to the loss of customer trust and significant financial losses. By conducting ethical hacking (hiring a white hat hacker) and penetration testing, organizations can identify and fix potential vulnerabilities before malicious actors can exploit them. Organizations can engage with a professional service provider with experience conducting such tests to implement ethical hacking and penetration testing. They can also provide training to their employees on how to identify and report potential security threats.
By regularly conducting ethical hacking and penetration testing, organizations can ensure that their security measures are up-to-date and effective against emerging threats. It also demonstrates a commitment to protecting sensitive data and building trust with customers and stakeholders.
Final Words
In this digital age, code and data protection are crucial to safeguard sensitive information from cyber threats. The constantly evolving cybersecurity landscape demands organizations to implement measures to protect their assets proactively.
The 10 tips discussed above, ranging from providing employee cybersecurity training to implementing regular vulnerability assessments, are effective ways to ensure code and data protection. Organizations must realize that cybersecurity is an ongoing process that requires continuous efforts to stay ahead. Failing to protect against cyber threats can result in data breaches, loss of reputation, and financial loss. Therefore, it is essential to implement the recommended tips to enhance code and data protection measures. Regular vulnerability assessments and employee cybersecurity training can reduce the risk of cyber-attacks and ensure compliance with regulatory requirements. Organizations must prioritize code and data protection to protect their assets and stakeholders. By implementing the recommended tips and being proactive, organizations can safeguard themselves against potential cyber threats and ensure the safety and security of their data and systems.
Related Posts:

